Hydra (the sea serpent) constellation is the largest among all the 88 modern constellations, 1303 square degrees wide and 100 degrees long. Although large, it does not contain any particularly bright star of the night sky. Alphard (an orange giant), is a moderately bright star, followed by Gamma Hydrae (a yellow giant), and Beta Hydrae (a blue-white star). Epsilon Hydrae is a bright binary star, and 27 Hydrae is a triple star. Among its variable stars, we can name R Hydrae, U Hydrae (a semi-regular variable star), and V Hydrae (home to two exoplanets). GJ 357 contains three exoplanets, including one super-earth (GJ 357 d) lying in the star’s habitable zone.
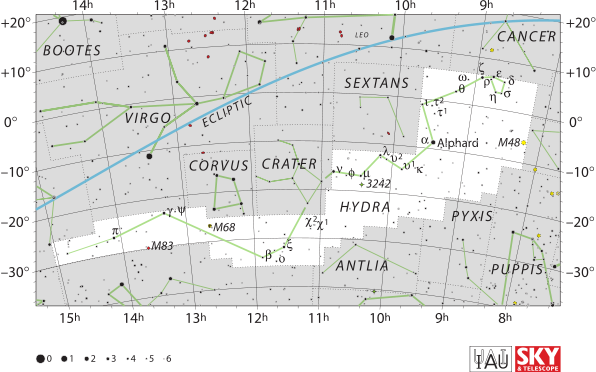
The Hydra constellation contains some deep-sky objects, among which is the spiral galaxy M83 (Southern Pinwheel galaxy). M68 is a globular cluster in the vicinity of this galaxy. Other globular clusters of the cluster are: M68 (NGC 4590) and NGC 5694. Planetary nebulae NGC 3242 and Abell 33 also belong to this constellation. Its open cluster is M48 (NGC 2548). NGC 3314 is a particular case as it is composed of two galaxies that are not interacting but seem that way. ESO 510-G13 is a beautiful warped spiral galaxy, located 150 million light-years from Earth. There is also an important elliptical galaxy residing in this constellation named NGC 4993 in which two neutron stars merged and gave rise to several electromagnetic sources such as GW170817, GRB 170817A, and SSS17a.